 The growing amount and accessibility of data can be a significant contributor guiding internal audit toward its True North—or, as sometimes happens, too much data can result in taking internal audit off course when it is not effectively used. Today there are 2.7 zettabytes of data in the digital universe, and by 2020, big data is predicted to be 50 times what it is today.1 As business operations become more proficient in their use of both structured and unstructured data, analytics are informing decisions across the business in ways never before considered.
The growing amount and accessibility of data can be a significant contributor guiding internal audit toward its True North—or, as sometimes happens, too much data can result in taking internal audit off course when it is not effectively used. Today there are 2.7 zettabytes of data in the digital universe, and by 2020, big data is predicted to be 50 times what it is today.1 As business operations become more proficient in their use of both structured and unstructured data, analytics are informing decisions across the business in ways never before considered.
For many years, internal audit has focused on using data in limited ways to conduct analytics for fieldwork purposes—commonly known as computer-assisted audit techniques. With advancements in technology, ease of use, and affordability of tools, now more than ever internal audit can focus on building a keen sense of direction to leverage data in a way that provides greater business insights, increases efficiency, enhances monitoring activities, and allows the company to respond better to risks. Leveraging data is not a destination of its own, but rather a mindset shift to integrate data into the audit life cycle—from risk assessment to planning, fieldwork, execution, monitoring, and reporting.
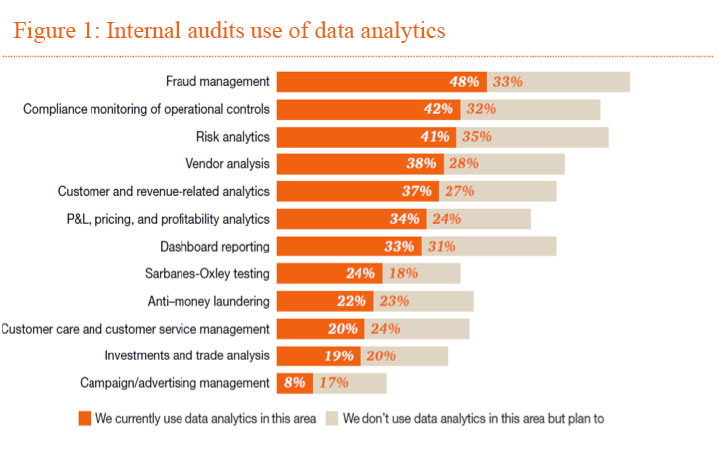
Our survey and interviews revealed that most, if not all, internal audit functions are thinking about how they can better leverage data to be not only more efficient but also far more effective. Most are experimenting with expanding its use, particularly in such areas as fraud management, compliance monitoring, and risk analytics (Figure 1). However, a critical difference between where internal audit functions are today and their True North lies in how data is being used. While 82% of chief audit executives (CAEs) report they leverage data analytics in some specific audits, just 48% use analytics for scoping decisions, and only 43% leverage data to inform their risk assessment. Thus, many still report they have a substantial journey ahead.
Internal audit functions that are evolving in pace with the business are more advanced in their use of data, including wider application across the audit life cycle. For example, risk identification has traditionally been done through a combination of executive meetings and the use of limited financial data. Internal audit functions that are headed toward True North are using data to identify where risks reside in the organization in order to determine where they should focus their efforts. They are also leveraging data not only to focus on where and what could be audited but also to decide whether auditing is needed at all. Ultimately, success with data is predicated on connecting data to insights about the business and the risks it is facing.
CAEs report that obtaining data skills is a top challenge. While 65% of CAEs report they have some data skills on their team, either in-house or through third parties, our interviews revealed a lack of the combined business acumen and data skills. Internal audit functions with sufficient size and scale are reporting the ability to invest in a combination of in-house and third-party resources, while many are turning completely to third parties to gain more immediate access to business-minded data skill sets.
Enhancements in tools have made it easier and more intuitive for business users to access data and gain comfort with how data can be leveraged. By providing a better view of risks, data visualization tools are enabling internal audit functions to absorb information in new and more constructive ways so they can identify and respond to emerging trends faster.
For those functions that are not far along the maturity curve of embedding data analytics into their audit life cycle, we have found that there is a need to work through various roadblocks, create quick wins, and gain momentum. In order to do this, many internal audit functions are still starting with pilot data programs.2 These pilots serve as proof of concepts for both stakeholders and those in the internal audit function. Pilots give practitioners the opportunity to work with data, get comfortable with it, and increase their creativity in thinking about how to use it. Sharing early wins with stakeholders will jump-start the momentum needed to drive more creative use of data.
1 “Infographic: The Explosion of Big Data,” sales-i, October 16, 2014, accessed January 26, 2015.
2 For more information on how to create best-in-class enterprise risk management, refer to PwC’s 2015 Risk in Review study.
 There is a particular type of Phishing attack which research teams see more and more often. This attack plays out as follows:
There is a particular type of Phishing attack which research teams see more and more often. This attack plays out as follows:
 We’ve entered into an age where network security breaches aren’t just common – they’re alarmingly more common than you think.
We’ve entered into an age where network security breaches aren’t just common – they’re alarmingly more common than you think.  A Seattle company was recently broken into and a stash of old laptops was stolen. Just a typical everyday crime by typical everyday thieves. These laptops weren’t even being used by anyone in the company. The crime turned out to be anything but ordinary when those same thieves (cyber-criminals) used data from the laptops to obtain information and siphon money out of the company via fraudulent payroll transactions. On top of stealing money, they also managed to steal employee identities.
A Seattle company was recently broken into and a stash of old laptops was stolen. Just a typical everyday crime by typical everyday thieves. These laptops weren’t even being used by anyone in the company. The crime turned out to be anything but ordinary when those same thieves (cyber-criminals) used data from the laptops to obtain information and siphon money out of the company via fraudulent payroll transactions. On top of stealing money, they also managed to steal employee identities. Microsoft is launching their second annual Small Business video contest, and we need your help. Last year we launched our first small business video contest with a simple request for small businesses to share their business stories via a 2-minute video. We reached 21 million people and had over 175 entries.
Microsoft is launching their second annual Small Business video contest, and we need your help. Last year we launched our first small business video contest with a simple request for small businesses to share their business stories via a 2-minute video. We reached 21 million people and had over 175 entries. Sooner or later every organization is faced with a technology or organization change
Sooner or later every organization is faced with a technology or organization change 


 Pick One Platform
Pick One Platform The subject of “leadership” is an interesting one and many people have offered their opinions.
The subject of “leadership” is an interesting one and many people have offered their opinions. With the rapid advance of consumer technology in recent years, customer demand for new technology solutions in the workplace has increased dramatically. For support organizations, this has created new challenges to provide technology related services while maintaining security and providing greater customer service. This problem is magnified for higher education Information Technology (IT) support groups who are struggling to keep up with customer technology demand in an environment where the academic culture is very permissive but resources dedicated to change are limited. Curtis Bonk, Ph.D., Professor of Instructional Systems Technology at Indiana University, states that educators have an ethical obligation to consider using technology to enable students’ learning. Higher education IT organizations have the same obligation to consider the use and support of technology for enabling both students’ learning and empowering instructors’ use of technology to achieve these outcomes. Providing good customer service while meeting this obligation represents the major challenge to higher education IT support organizations.
With the rapid advance of consumer technology in recent years, customer demand for new technology solutions in the workplace has increased dramatically. For support organizations, this has created new challenges to provide technology related services while maintaining security and providing greater customer service. This problem is magnified for higher education Information Technology (IT) support groups who are struggling to keep up with customer technology demand in an environment where the academic culture is very permissive but resources dedicated to change are limited. Curtis Bonk, Ph.D., Professor of Instructional Systems Technology at Indiana University, states that educators have an ethical obligation to consider using technology to enable students’ learning. Higher education IT organizations have the same obligation to consider the use and support of technology for enabling both students’ learning and empowering instructors’ use of technology to achieve these outcomes. Providing good customer service while meeting this obligation represents the major challenge to higher education IT support organizations. The growing amount and accessibility of data can be a significant contributor guiding internal audit toward its True North—or, as sometimes happens, too much data can result in taking internal audit off course when it is not effectively used. Today there are 2.7 zettabytes of data in the digital universe, and by 2020, big data is predicted to be 50 times what it is today.1 As business operations become more proficient in their use of both structured and unstructured data, analytics are informing decisions across the business in ways never before considered.
The growing amount and accessibility of data can be a significant contributor guiding internal audit toward its True North—or, as sometimes happens, too much data can result in taking internal audit off course when it is not effectively used. Today there are 2.7 zettabytes of data in the digital universe, and by 2020, big data is predicted to be 50 times what it is today.1 As business operations become more proficient in their use of both structured and unstructured data, analytics are informing decisions across the business in ways never before considered.
 Technology has transformed the way we do almost everything. And yet, all too often, we resign kids to a use-only mode. Teaching students to create, rather than consume—to understand how technology works, not just how to use it—serves to strengthen a host of lifelong skills like logic, problem solving, creativity, and critical thinking. You see that kid playing on his computer? He may be the next Steve Jobs. And that teenage girl building a robot? She may discover a new advancement in biomedical engineering. But those possibilities may become realities only if we are able to help them connect the dots from playing with technology to using it to create something new to real world jobs.
Technology has transformed the way we do almost everything. And yet, all too often, we resign kids to a use-only mode. Teaching students to create, rather than consume—to understand how technology works, not just how to use it—serves to strengthen a host of lifelong skills like logic, problem solving, creativity, and critical thinking. You see that kid playing on his computer? He may be the next Steve Jobs. And that teenage girl building a robot? She may discover a new advancement in biomedical engineering. But those possibilities may become realities only if we are able to help them connect the dots from playing with technology to using it to create something new to real world jobs.